Dec 1, 2021
In conjunction with Critical Infrastructure Month, let’s spotlight the important yet underrated topic of cybersecurity in critical infrastructure.
Critical infrastructures are a vital part of our daily lives. With many of the sectors going through digitalization and expanding their capabilities with the latest technologies, they become culpable to cyber attacks. Before going in-depth with your security team, find out a few basics about critical infrastructure cybersecurity: what is it, how significant, the challenges, and the solutions.
What Is Critical Infrastructure?
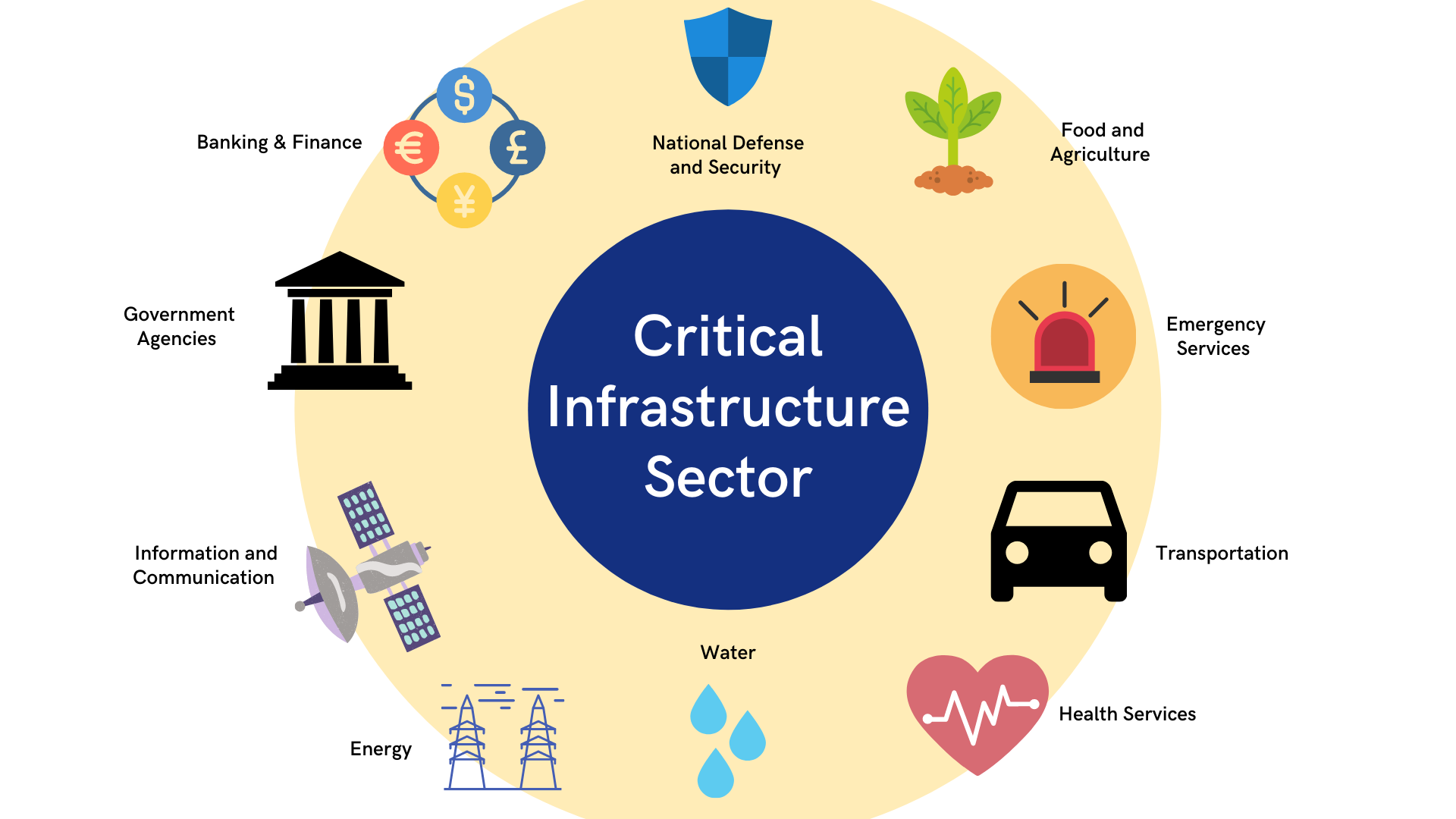
Critical infrastructure, by definition, is the systems and assets, regardless of physical or virtual form, that is essential to the point that if incapacitated or destroyed, would cause a devastating impact on the national economy, security, public health and safety, or even affect national economic, security, public health and safety any combinations of those matters. In Malaysia, the ten sectors that made up the nation’s Critical National Information Infrastructure (CNII) are:
With many adapting to the Fourth Industrial Revolution (Industry 4.0), cyber security in critical infrastructure has become more important, especially with the change from manual machines and tasks to operational technology and the use of IoT devices. This is moved forward further due to the increasing demands and needs, both within the nation and globally.
Cyber security in critical infrastructure encompasses three risk factors: the people, process, and technology. These include the equipment, applications, management systems, employees, and vendors. The technologies used are considered as operational technologies (OT), industrial control systems (ICS), and supervisory control and data acquisition (SCADA), an architecture comprising of computers, networked data communications and graphical user interfaces for controlling machines and processes, commonly used in processing plants.
The Challenges and Risks Faced by Critical Infrastructure
According to the 2021 Global Threat Intelligence Report (GTIR), manufacturing had become the second most targeted industry. In 2013, an essential dam in the U.S.A. was hacked through their SCADA systems, which allowed attackers to control the floodgates remotely. In December 2015, thousands of homes in Ukraine faced six hours of power outages due to the BlackEnergy malware. In Verizon Data Breach Investigation Report 2019, it was reported that out of 352 data breach incidents, 87 of them were manufacturers.
Among the common cyber security threats and flaws that cause these attacks were legacy, outdated and misconfigured devices, breaches in third-party vendors, and lack of security assessment towards their assets, management system, and awareness. The impact of an attack on these systems could range from critical losses through downtime and production delays, human safety hazards and equipment damages. Hence, the importance of a manufacturing security system.
This proves an unsettling fact; critical infrastructure sectors are being actively attacked while being insufficiently secured. With many implementing IoT devices to reach the revolution of Industry 4.0, these increase the area of attacks for malicious hackers. With money and fame to gain, and without physically exerting themselves, these attackers can conduct nationwide attacks from the comfort of their seats.
Cyber Security Measures in Critical Infrastructure
Understanding the importance of cyber security in critical infrastructure, countries worldwide have enacted relevant policies to ensure organizations adhere to minimum security standards or be responsible for their negligence. For example, the U.S.A. had released a Cybersecurity Executive Order and a private-public cybersecurity partnership in their 100-Day Electric Plan, answering the previous cyber security attack on the US power grid.
In Malaysia, a National Cyber Security Policy (NCSP) was formulated in 2006 to address the risks towards CNII entities. It is important for critical infrastructure entities in Malaysia, recognized as CNII entities, to obtain MS ISO/IEC 27001:2007 Information Security Management System (ISMS) certification. This certification and implementation are enforced by the Malaysian Communications and Multimedia Commission (MCMC) since February 2010.
In 2018, the Industry4WRD National Policy was launched by the Ministry of International Trade and Industry (MITI), in response to the nation’s need to broaden the cyber security capabilities by establishing a set of cyber security and IoT guidelines for Industry 4.0
To support this, Cyber Security Malaysia had released several guidelines for industrial sectors, which are:
- Guidelines for Secure Industrial Control System (ICS)
- Guidelines for Secure Internet of Things (IoT)
- Guidelines for Secure Industry 4.0
Cyber Security Malaysia strategic partners are also helping to bridge the knowledge and security gap by offering assessments and consultations on OT security and ensuring industrial players adhere to the latest ICS security standards and certifications.
In conclusion, cyber security in critical infrastructure is more important than ever, and shouldn’t be overlooked. A security posture assessment should be done, at least bi-annually, covering the assets, the people, and all third parties involved that have access to the organization’s operational data.
To know more about safer and hardening your cyber security according to your sector’s needs, reach out to YNY Technology, a MITI Industry4WRD Certified Readiness Assessor body, and Cyber Security Malaysia Strategic Partner, industrial cybersecurity experts here.