November 9, 2021
Industrial players are becoming more aware and adapting to the needs and demands of customers through IT/OT convergence. It helps increase manufacturing capabilities, handle a larger workload, and better efficiency. However, these also increase the chances of being victim to cyber threats, especially with manufacturing ranked as the second most targeted by cyber attacks. There are also fears of disruptions in operations while adapting a better cybersecurity posture. How can industrial players and their IT teams handle these conundrums?
On and off, there are several attack surfaces in the industrial control systems. With so many attack vectors, there is, however, no silver bullet for cybersecurity. It needs joint forces from the management to individual levels and from the edge to the cloud to ensure industrial cybersecurity countermeasures are in place.
On Nov 9, Our OT cybersecurity consultant, Gary Kong, had been given the opportunity to discuss this matter through a 16 minutes security talk with Moxa Security’s Jesse Ku. The discussion provides further understanding on the importance of cybersecurity in operational technology and its convergence, while also answers on how it can be implemented without affecting the operations.
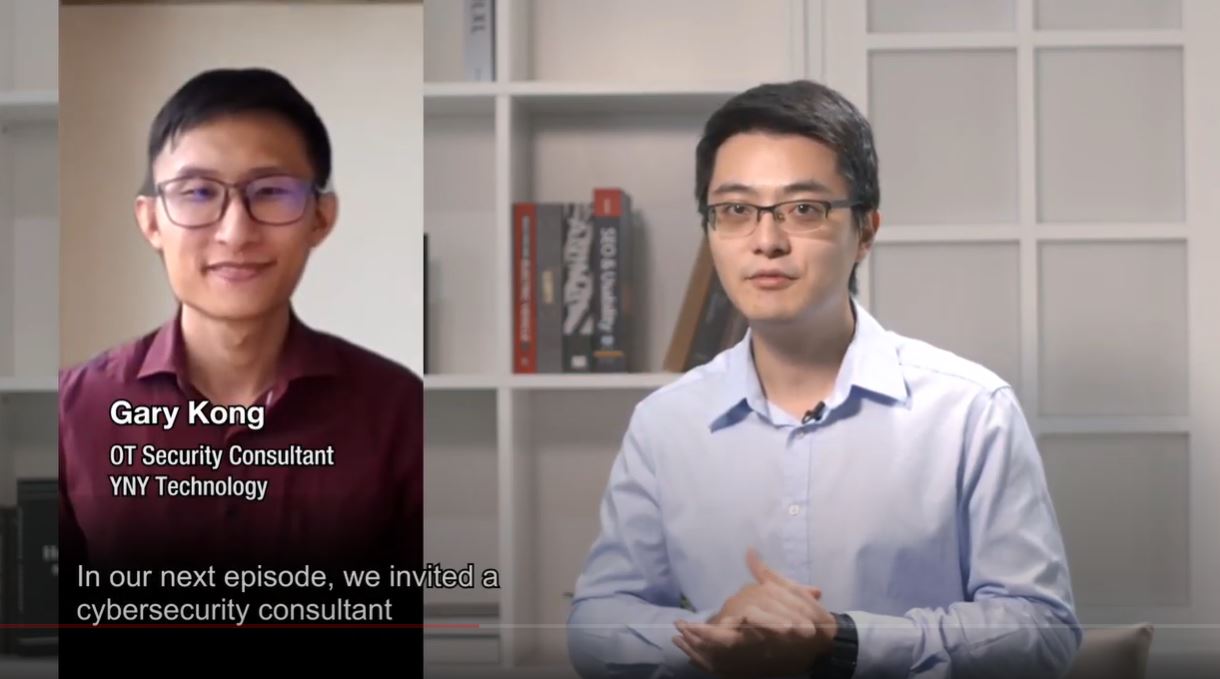
This security talk covers:
- Changes in the industrial cybersecurity landscape
- Risks and challenges that comes with IT/OT network convergence
- Impact on operations performance
- Common cybersecurity flaws discovered during assessments
- The importance of health check
- How to choose the best solutions
- Tips on security for industry (especially in getting ready for Industry 4.0)
Check out the latest Security Talk show by MOXA, and let us see what the expert has noticed the changes of the cybersecurity landscape in the industrial control systems / network during these past 3 – 5 years.
YNY Technology Provide ICS Security Health Check
ICS Security health check helps to identify local and remote OT devices undiscovered in your asset list and detect security blind spots that existed on the device discovered. ICS risks are evaluated to help you to identify ICS threats relevant to your current environment and able to focus on the implementation of effective security control measures.
You may CONSULT US to know how to Protect your ICS Environment from potential cyber threats with YNY GoDigital Defense-In-Depth Security Solution.